close
先用 YUM 裝套件
# rpm -qa |grep ldap nss-pam-ldapd-0.8.13-8.el7.x86_64 openldap-clients-2.4.40-13.el7.x86_64 openldap-2.4.40-13.el7.x86_64
確定 nsswitch 有 ldap
# cat /etc/nsswitch.conf |grep ldap passwd: files sss ldap shadow: files sss ldap group: files sss ldap netgroup: files sss ldap automount: files ldap
有設 /etc/openldap/ldap.conf (加上去 URL , BASE)
URI ldap://192.168.0.200 BASE dc=tw,dc=demo
檢查 /etc/pam.d/password-auth
# cat /etc/pam.d/password-auth |grep ldap auth sufficient pam_ldap.so use_first_pass account [default=bad success=ok user_unknown=ignore] pam_ldap.so password sufficient pam_ldap.so use_authtok session optional pam_ldap.so
檢查 /etc/pam.d/system-auth
# cat /etc/pam.d/system-auth |grep ldap auth sufficient pam_ldap.so use_first_pass account [default=bad success=ok user_unknown=ignore] pam_ldap.so password sufficient pam_ldap.so use_authtok session optional pam_ldap.so
設定 /etc/nslcd.conf
# Local user account and group, nslcd uses. uid nslcd gid ldap # Active Directory server settings (SSL encryption) uri ldap://192.168.0.200:389/ tls_reqcert allow base dc=tw,dc=test # LDAP bind account (AD account created in earlier) binddn cn=Administrator,cn=Users,dc=tw,dc=test bindpw P@ssw0rd # Mappings for Active Directory pagesize 1000 referrals off filter passwd (&(objectClass=user)(!(objectClass=computer))) map passwd uid sAMAccountName map passwd gecos displayName map passwd homeDirectory "/home/$uid" map passwd loginShell "/bin/bash" filter shadow (&(objectClass=user)(!(objectClass=computer))) map shadow uid sAMAccountName map shadow shadowLastChange pwdLastSet filter group (objectClass=group) map group gidNumber gidNumber map group member sAMAccountName
停止 nslcd.服務用 denug mode
# systemctl stop nslcd
# nslcd -d
nslcd: DEBUG: add_uri(ldap://192.168.0.220:389/)
nslcd: DEBUG: ldap_set_option(LDAP_OPT_X_TLS_REQUIRE_CERT,3)
nslcd: version 0.8.13 starting
nslcd: DEBUG: unlink() of /var/run/nslcd/socket failed (ignored): No such file or directory
nslcd: DEBUG: initgroups("nslcd",55) done
nslcd: DEBUG: setgid(55) done
nslcd: DEBUG: setuid(65) done
nslcd: accepting connections
測試 nslcd.服務
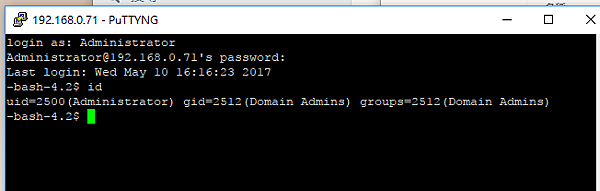
# getent passwd |grep Administrator Administrator:*:2500:2512::/home/:/bin/bash # su - Administrator -bash-4.2$ id uid=2500(Administrator) gid=2512(Domain Admins) groups=2512(Domain Admins) -bash-4.2$ exit logout #
看 debug 內容
# nslcd -d
nslcd: DEBUG: add_uri(ldap://192.168.0.200:389/)
nslcd: DEBUG: ldap_set_option(LDAP_OPT_X_TLS_REQUIRE_CERT,3)
nslcd: version 0.8.13 starting
nslcd: DEBUG: unlink() of /var/run/nslcd/socket failed (ignored): No such file or directory
nslcd: DEBUG: initgroups("nslcd",55) done
nslcd: DEBUG: setgid(55) done
nslcd: DEBUG: setuid(65) done
nslcd: accepting connections
nslcd: [8b4567] DEBUG: connection from pid=23866 uid=0 gid=0
nslcd: [8b4567] <sess_c="Administrator"> DEBUG: nslcd_pam_sess_c("Administrator","su-l",12345)
nslcd: [7b23c6] DEBUG: connection from pid=23866 uid=0 gid=0
nslcd: [7b23c6] <passwd="Administrator"> DEBUG: myldap_search(base="dc=tw,dc=test", filter="(&(&(objectClass=user)(!(objectClass=computer)))(sAMAccountName=Administrator))")
如果沒問題就 ctrl-c 關閉用 systemctl restart nslcd 啟動 , 寫入開機 .........
後記 : home 沒有辦法正確 ........XD
還有些帳號
nslcd: [1b58ba] <passwd(all)> CN=Admin,CN=Users,DC=tw,DC=test: uidNumber: missing
沒辦法使用 ......!@#$%^&*()
全站熱搜


 留言列表
留言列表


